Ensure proper route table configuration
While setting the right rules in security groups or NACLs is a good practice, it is equally important to ban unwanted connectivity using properly defined route tables. This is because route tables provide an additional layer of security controls. For instance, even if a security group ends up being misconfigured, a well-configured route table can still prevent unwanted network access. This highlights the importance of route tables as a critical security control within your VPCs.
One of the fundamental principles in security is the principle of least privilege. This principle asserts that a system should be granted the bare minimum levels of access necessary to perform its tasks. This principle is crucial when configuring route tables in your VPC. For example, if a subnet does not require internet communication, it should not possess a route to an IGW or a NAT gateway. The same approach applies to connectivity outside of your VPC, such as VPC peering or VPN connection. If a specific subnet does not require access to these external networks, no route should be established to access them from that particular subnet.
Centralize network traffic management in multi-VPC environments
In complex environments featuring multiple VPCs and accounts, centralizing network traffic management becomes paramount for maintaining robust security and simplifying operational demands. Using a transit gateway emerges as a pivotal solution, serving as a centralized hub through which all inter-VPC traffic is routed. This consolidation facilitates several critical security practices:
- Streamlined connectivity control: Centralizing network traffic via the transit gateway enables organizations to ensure that all inbound and outbound communications from VPCs pass through this single point.
- Traffic inspection and filtering: Integrating AWS Network Firewall along with additional services, such as AWS Shield and AWS WAF, through the transit gateway allows organizations to inspect and filter all traffic traversing the central hub. This setup enforces uniform security policies, ensuring that only authorized and clean traffic flows between VPCs, thereby offering a strong defense against potential threats and malicious activities.
- Regulated access with route tables: To further enhance security, modifying the route tables in each VPC to direct all traffic (0.0.0.0/0) to the transit gateway ensures comprehensive routing through the transit gateway. This measure prevents any direct access between VPCs or from VPCs to the internet that bypasses centralized security controls.
- Compliance and policy enforcement: In multi-account environments, the centralized management model supports compliance and security policy enforcement across the organization. The combination of service control policies (SCPs) and AWS Config plays a crucial role in ensuring and monitoring that the applied route tables consistently redirect all the network traffic via the transit gateway, providing an additional layer of security governance.
- Centralized VPC endpoint deployment: This involves deploying VPC endpoints in the central hub, rather than in individual VPCs, to enhance secure communications with AWS services. This strategy avoids public internet exposure and leverages the transit gateway for efficient and centralized access control.
The following diagram (Figure 2.3) illustrates a setup where multiple VPCs are interconnected through a central hub VPC via the transit gateway, facilitating centralized internet access and access to AWS services through VPC endpoints. This hub employs AWS Network Firewall, among other services, to screen all passing traffic:
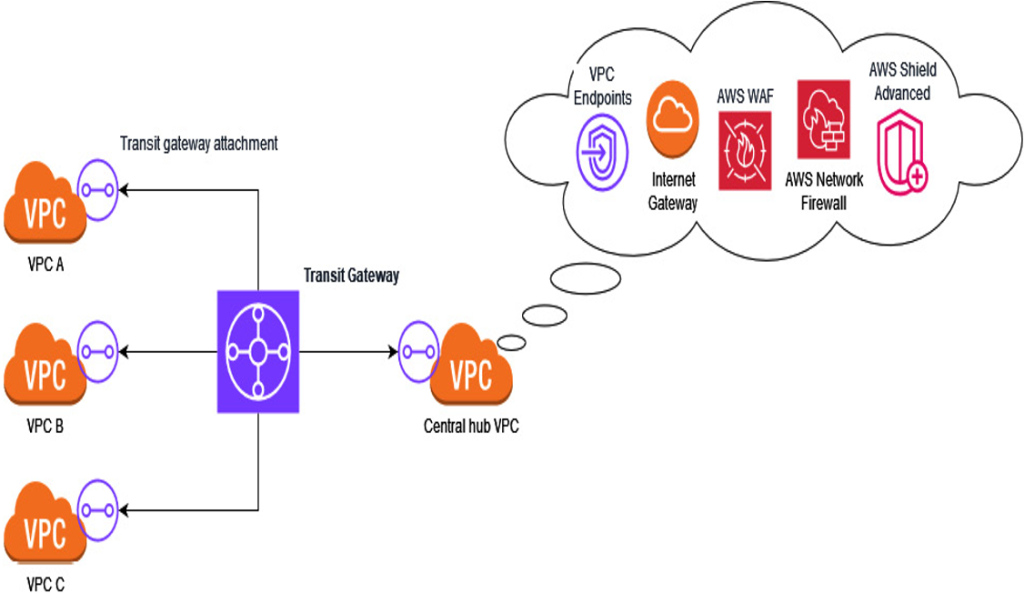
Figure 2.3 – Centralized multi-VPC network architecture