Regularly review and update your configuration
Maintaining secure VPCs is not a one-time task but an ongoing process. As your business needs evolve, so will your configuration. Moreover, the threat landscape is constantly evolving with new vulnerabilities and attack vectors. Therefore, it is crucial to continuously monitor and update your configuration to ensure it remains aligned with your security requirements and the evolving threat landscape.
Regular audits of your configuration should be conducted to identify any potential security gaps. These audits should include checking the security groups and NACLs for any overly permissive rules, reviewing the route tables for any unnecessary routes, and verifying that all resources are in the correct subnets. Any misconfigurations identified during these audits should be corrected promptly to minimize the risk of a security breach. In addition to manual audits, consider leveraging other services. AWS Config, for instance, can be used to continuously monitor the configuration of your VPC resources and evaluate them against desired states.
Finally, remember that security is a shared responsibility. While AWS provides a variety of tools and services to help secure your VPCs, it is ultimately up to you to use these tools effectively.
Shifting from VPC design to its armor, it is time to delve into the essential security mechanisms for network traffic filtering.
Implementing security groups, NACLs, and AWS Network Firewall
Continuing our journey through this chapter, let’s focus on the effective implementation of security groups, NACLs, and AWS Network Firewall. These three components are pivotal in ensuring robust protection of your resources within your VPCs, each playing a distinct role in managing and filtering network traffic. In this section, we will clarify their roles, interactions, differences, and overlaps, and provide guidelines for their effective implementation.
First, let’s demystify these three mechanisms:
- Security groups: These act as virtual firewalls at the ENI level for AWS resources within a VPC, managing both inbound and outbound traffic. Unlike traditional host-based firewalls that are implemented within the operating system (OS), security groups are managed through the AWS management plane, providing enhanced security by being less susceptible to compromise. Security groups are stateful, allowing automatic inbound response to outbound requests based on rule-defined criteria.
- NACLs: These function at the subnet level to control inbound and outbound traffic for all resources within a subnet. NACLs are stateless, requiring explicit allowance of both request and response traffic in the rules for two-way communication.
- AWS Network Firewall: This is a paid feature for VPCs that offers a more granular level of traffic control. It enables the creation of detailed rules for inspecting and filtering traffic based on attributes such as domain names and IP addresses. The firewall not only analyzes packet metadata but also its contents, offering advanced decision-making capabilities for allowing or denying traffic. This provides a powerful tool for managing your VPC traffic and enhancing its security to meet the most advanced requirements.
The following table (Table 2.2) offers a side-by-side comparison of the aforementioned components, along with their respective use cases:
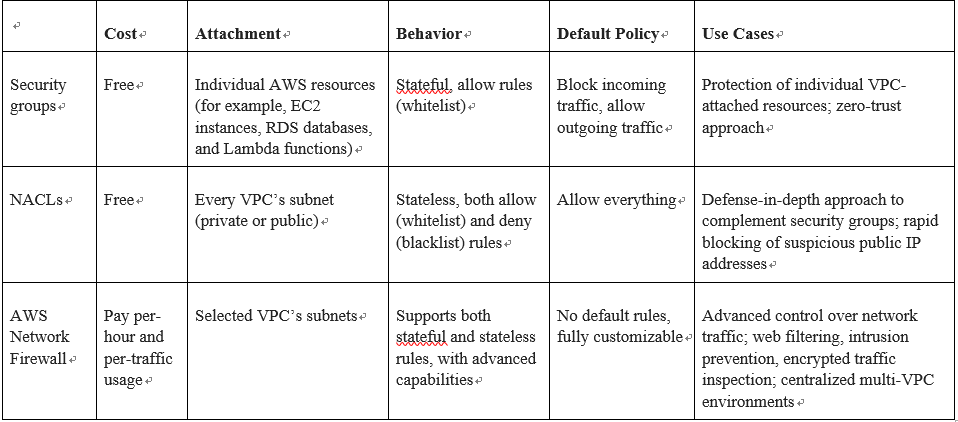
Table 2.2 – Security groups, NACLs, and AWS Network Firewall comparison
The following diagram (Figure 2.4) depicts how a VPC’s security infrastructure is established, showcasing security groups linked to each ENI and NACLs applied across subnets. It highlights the necessity for AWS Network Firewall to have endpoints in dedicated public subnets for each AZ, directing all traffic through these endpoints for comprehensive screening before reaching its destination, including private subnets, public subnets, or internet access. Note that the NAT gateways are no longer present in this VPC architecture as their function is now performed by AWS Network Firewall for all outbound traffic:
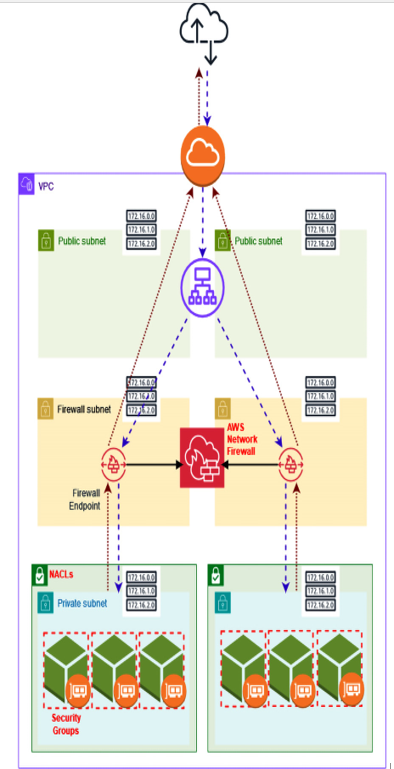
Figure 2.4 – Security groups, NACLs, and AWS Network Firewall integration
Building on this introduction, it is time to dig into the practicalities of working with each of these three essential security components.