Roles
An IAM role represents a unique and dynamic approach to handling permissions within AWS. Unlike traditional IAM users, roles don’t have a fixed identity tied to them. Instead, they act as containers for permissions that can be assumed by other identities such as IAM users and roles. This mechanism provides a flexible way to grant temporary access.
How IAM roles work
At the heart of IAM roles is the AWS Security Token Service (STS), which is instrumental in the dynamic issuance of temporary credentials. When an identity assumes a role, STS provides temporary credentials for use within a limited session duration. These credentials, which are time-bound and automatically rotated by STS, significantly bolster security by reducing the risk of compromise.
The operation of STS, while integral, typically occurs behind the scenes thanks to its seamless integration with IAM. This integration often negates the need for users to directly interact with STS. Central to utilizing IAM roles is the Assume Role action. This action is initiated when an identity (be it a human user, an application, or another AWS service) requires specific permissions to perform an action. To assume a role, the identity must satisfy the conditions defined in the role’s trust policy, which specifies who can assume the role and under what conditions. Once the trust policy conditions are met and the role is assumed, the identity is endowed with the permissions associated with that role for the duration of the session.
The following diagram (Figure 3.2) illustrates the following role assumption workflow:
- Assume Role request: A successfully authenticated identity submits an Assume Role request to STS.
- Temporary credentials: If the request complies with the associated IAM permissions and the requested role’s trust policy, STS grants the assumed role to the requesting identity and issues the associated temporary credentials.
- Resource access request: The requesting identity uses the provided temporary credentials associated with the assumed role to request access to AWS resources.
- Authorization check: IAM then evaluates the access request against the permissions linked to the assumed role, the requested resource, and the actions specified in the request. If authorized, IAM grants access to the resource:
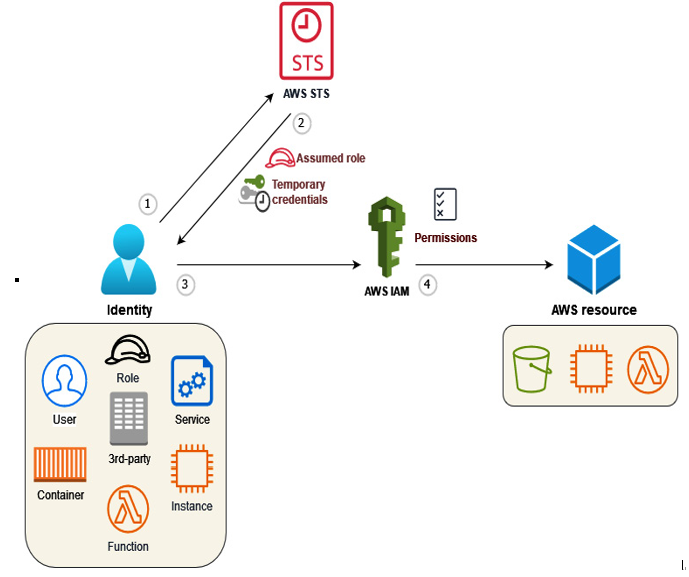
Figure 3.2 – The Assume Role workflow
By understanding how IAM roles work, you can leverage the benefits of secure, temporary access and fine-grained control within your AWS environment.