Understanding ABAC
ABAC is a flexible and granular access control model that uses attributes as building blocks in access control decisions. These attributes can be associated with a user, a resource, an environment, or a combination of these.
In the context of AWS, ABAC is particularly useful because it allows you to simplify permission management at scale. You can create policies that are narrowly tailored to allow only the necessary access instead of managing permissions for each user. For example, you might have a policy that allows developers in your organization to modify resources, but only in the development environment. This policy could be based on attributes such as user.Role=Developer and resource.Environment=development.
The following figure (Figure 3.1) shows an example of ABAC implementation based on tags assigned to users and resources. In this example, only users with the Team tag associated with the Blue value attached to them can access resources that have the same tag. The same logic applies to users with other tag values who can access their respective resources:
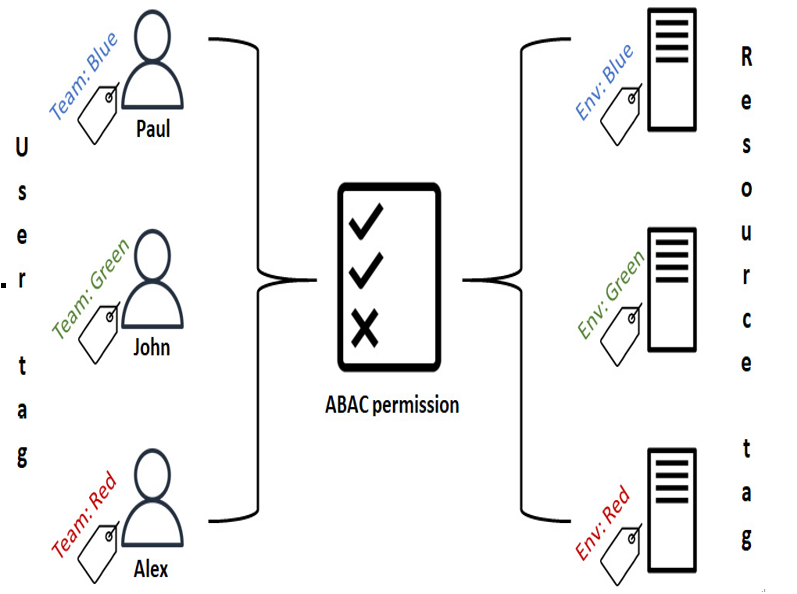
Figure 3.1 – ABAC example using tags
In addition, Amazon Cognito, an identity management solution for application users, simplifies managing end user identities and attributes. In tandem with IAM, it enables the creation of attribute-referencing policies, facilitating fine-grained access control in your applications running on AWS through ABAC. More details on integrating Cognito with IAM for ABAC will be covered in Chapter 8.
ABAC is also useful in scenarios where you need to grant access based on conditions that are evaluated at runtime. For example, you might have a policy that allows access to a resource only if the request comes from a specific IP address range.
Remember, when implementing ABAC, it is important to carefully manage your attributes and regularly review your policies to ensure they are granting the appropriate level of access.